کد:http://blog.msfirewall.org.uk/2008/06/using-cmak-to-configure-isa-server-vpn.html
Part 1: Creating the CMAK Profile
Amongst the many benefits of using ISA Server as your VPN gateway, a key attribute is the fact that the VPN client software is built into Windows which negates the need to install any third-party VPN client. The VPN connection can easily be configured within Windows using the New Connection Wizard, however I have always preferred the more elegant solution of using the Connection Manager Administration Kit (CMAK). This is a free tool included with Windows Server 2003 which can be used to create a CMAK profile (connectoid) that contains all of the the VPN connection properties, including a whole heap of customisation to make life easier and more intuitive for for users.
This blog entry is the first of a two part series which provides a walkthrough of creating a CMAK profile which can be used for connecting to an ISA Server VPN gateway. Once the CMAK profile has been created, part two of the series will look at customising the profile to add some useful features, cater for a better user experience and improve security. The blog entry assumes that the VPN feature of ISA Server has already been enabled and the L2TP/IPSec protocol has been enabled.
CMAK can be installed using the Add or Remove Programs control panel applet and is included under the Add/Remove Windows Components, Management and Monitoring Tools component.
Please Note: I have omitted wizard steps that can remain at their default settings to reduce the number of screenshots. Steps that are not included below can simply be accepted using the Next button.
Once opened, the wizard begins as shown below:
On the Service and File Names page, enter the desired Service Name and File name (this is also called the Short Service Name):
On the VPN Entries page, click the Edit button:
Select the Security tab on the Edit Virtual Private Networking Entry window and then change the Security Settings drop down selection to Use advanced security settings:
Once selected, click Configure next to the Advanced security settings text.
If you are planning on using a simple authentication method comprising of a Windows user name and password, configure the Advanced Security Settings options as shown below.
These settings represent a baseline level of security for the VPN connection, but does not represent a high security or recommended deployment. In terms of authentication, many organisations require that VPN connections are subject to some form of two-factor authentication to mitigate the risks of static user names and passwords. In addition, although it is possible to choose the Only use Point to Point Tunneling Protocol (PPTP) option, I would no longer recommend using this method as many security/penetration tests now highlight PPTP as a poor VPN solution in terms of security. As we are using simple authentication, we are unlikely to be able to provide certificates for L2TP, so we need to use enable the Use a pre-shared key when using L2TP/IPSec option in this scenario.
If you are lucky enough to be able to provision certificates (due to the use of an internal Public Key Infrastructure (PKI) deployment perhaps) then the following Advanced Security Settings options are recommended as a more secure alternative to the above:
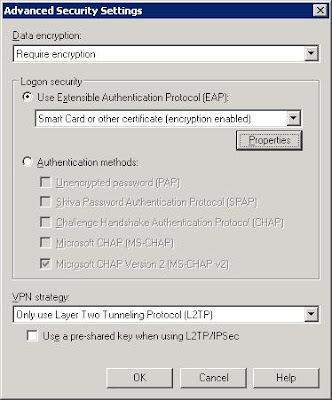
In this scenario, we are using certificates to enable user and machine authentication for the VPN connection, as this provides a much higher level of security. It is outside the scope of this entry to provide specific details of the necessary PKI infrastructure and certificates that are required, but if you would like to see these details, please leave comments and I will try and add more detail in future blog entries.
Please Note: In addition to these two options, it is also possible to integrate third-party authentication solution into CMAK. From personal experience, I have also used RSA SecurID which integrates well (after a little work!) to provide a seamless solution. More information on this option can be found here.
If you have chosen to define a pre-share key for L2TP/IPSec then the Pre-shared Key page will be displayed. Enter the required pre-share key into the Enter key field. In order to protect the key and ensure it is encrypted in the CMAK profile files, is it recommended to choose the Encrypt the pre-share key with a PIN option. Once enabled, this PIN will need to be entered by any user that wishes to install the CMAK profile (example of this later).
On the Phone Book page, deselect the Automatically download phone book updates as this is not required.

This final step of the completed wizard is shown below:
With the wizard completed, it is simply a matter of distributing the CMAK self-installing executable (defined in the path above) to users.
Once users receive the file, they can simply run the executable to receive the following prompt shown below. Click Yes to install the CMAK profile.
If you chose the Encrypt the pre-share key with a PIN option during the wizard, you will be asked to enter the PIN. Entering an incorrect PIN will cause the installation to terminate.
On the next step, I would recommend selecting the My use only option.
Once installed, a new Connection Manager pane will be shown within Network Connections (example shown below from Windows XP) which contains the new 'ISA Server VPN' VPN connectoid.
After successful installation, the VPN connection will also be initiated/connected and you will be presented with the following connection:
You will notice that the Save password option is enabled by default. For obvious reasons, this represents a security risk which we will cover in the next blog entry.
So, we now have a basic CMAK profile defined and the VPN connectoid has been installed which provides a good platform for part two of this blog series. In part two, we will look at customising the CMAK profile to include some advanced features, add support for ISA Server VPN gateways behind NAT devices and improve security by disabling features like the Save password option shown above...
Additional information on the Connection Manager Administration Kit (CMAK) can be found here.
موضوعات مشابه:
- Configuring Automatic Discovery for ISA Server Clients ?
- Clients receives error 691 trying to connect to ISA Server 2006 as VPN Server
- Clients receives error 691 trying to connect to ISA Server 2006 as VPN Server
- مشکل Citrix Clients و ISA Server


 LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks


