By default, the Microsoft ISA Server firewall is configured to deny all traffic that is not explicitly permitted by an access rule. This means that the firewall administrator will need to configure a number of access rules in order to facilitate domain and client communication, among other things.
Thankfully the ISA firewall includes a set of
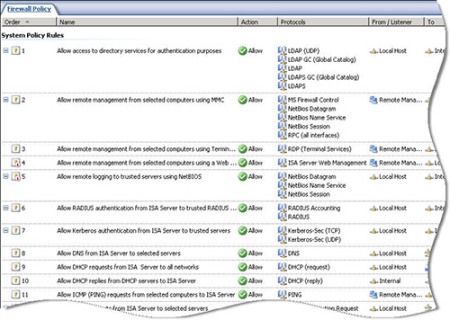
system policy access rules that simplify the configuration and operation of the firewall. The system policy contains a set of pre-configured access rules that allow ISA and the underlying operating system to communicate with things such as domain controllers, DNS servers, authentication servers, etc. The system policy rules are hidden from view by default. If you wish to see the system policy rules themselves, right-click on the
‘Firewall Policy’ node, highlight
‘View’, and then select
‘Show System Policy Rules’.

To edit the system policy rules, right-click on the
‘Firewall Policy’ node and choose
‘Edit System Policy…’.

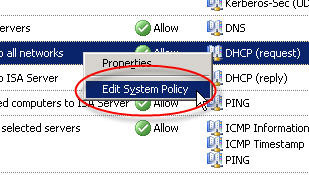
If you have chosen to display the system policy rules you can double-click any rule or right-click a rule and choose
‘Edit System Policy’ to bring up the system policy editor as well.
Although having pre-configured system policy rules is convenient, some of the rules are broad or may not be required in your environment. I would highly recommend that you review and edit the system policy prior to deploying a production Microsoft ISA firewall. For example, by default the system policy is configured to allow DHCP requests from the ISA firewall to the Internal network.
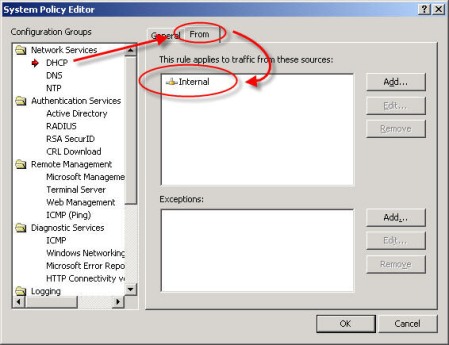
From a security perspective it would be best to specify which DHCP servers your ISA firewall can communicate with. Create new computer objects for each of your DHCP servers and specify them as the source for this rule instead of the entire Internal network. If none of your firewall’s network interfaces are configured to use DHCP you can safely disable this rule.
Another instance where the system policy can be tightened up is the DNS system policy rule. By default this rule allows the ISA firewall to communicate to DNS servers on all networks – and that includes the
external network!
(see Jason Jones’ blog post on proper ISA firewall network configuration)

This is an excellent opportunity to improve the security posture of your ISA firewall. I would recommend that you specify which DNS servers the ISA firewall can communicate with explicitly. Create new computer objects for each of your DNS servers and specify them as the destination for this rule, removing of course the
‘All Networks (and Local Host)’ network object.
One more example of broad system policy configuration is the SMTP system policy rule. By default this rule allows the ISA firewall to communicate to any SMTP server on the Internal network.

Again, your configuration will be much more secure if you specify which SMTP servers the ISA firewall can communicate with. If you are not using STMP notifications on the ISA firewall you can safely disable this rule.
These are only a few examples of areas where the system policy rule set can be tightened to improve security on the ISA firewall. Once you have completed your initial configuration, I would strongly encourage you to review and edit these policies. By disabling unnecessary rules and restricting the access on others you can enhance the already secure configuration of the ISA firewall.


 LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks









