How to use Group Policy Preferences to Secure Local Administrator Groups
One problem I see all the time is IT administrator never being able to control who is a local administrator of any particular computer. The problem is that when you give someone local admin access to a computer (because they legitimately need it) you cant stop them from giving admin access to someone else on the same computer. When this does happen it is also its almost impossible to discover as you have to run a query every computer to see who is in the local admin group and then figure out which account should be a member. Once solution to this is of course following Microsoft best practice and not give your users local admin access to their PC or Server and in an utopian environment this would be possible but we all live in the real world where managers have admin access to their PC’s and developers are allowed to install any software they want. So how do you give a users full admin access to a computer but stop them from adding more people to the local admin group on a computer?Use Group Policy Preference of course.
But first a bit of History… Since Group Polices were first introduced with Windows 2000 there was an setting called “Restricted Groups” which allows you to control the membership of a group. This option had two modes one called “Members” option which I also call the “Iron Fist” mode and the other “Members Of” option which is much gentler. The “Members” option removes any groups or users that are not explicitly specified and the “Members Of” option just adds a specific group which out removing any existing groups. The “Members” option was really good at cleaning up those rogue members of the local admin group but its was also really hard to setup as you had to have a new group policy every time you wanted a different list of members in local group on a computer. The “Members Of” option was a lot easier to maintain as you could layer multiple group policies on top of each other but this normally resulted in just adding another layer of group to the pile of groups that were already in the local administrators group. The other problem was the “Members” option would override the “Members Of” option so there was really no way of mixing the two modes.
BUT… Group Policy Preferences can use Variables which enabled you to be very extremely granular in controlling you local admin group while still having “Iron Fist” control. Muuhhaaaahahahahah!!!
How do I setup a restricted local administrator group?
The following steps will need to be applied to a GPO that is applied to the computer objects you want to control the local administrator groups. Note: You must make sure you don’t have any other Group Policy “Restricted Groups” settings applied to your computers as they will always override the group policy preferences settings.
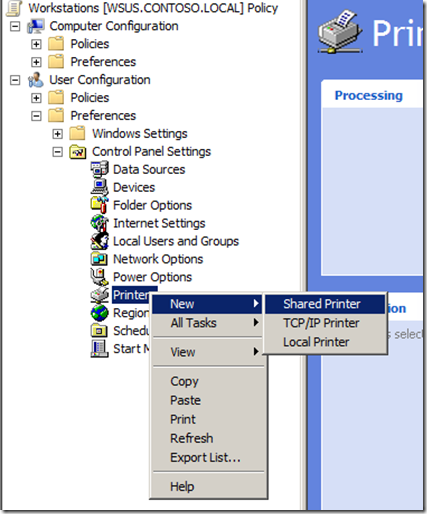
Step 1. Open the Group Policy Management Consol and edit the group policy that is applied to the scope of computers that you want to control.
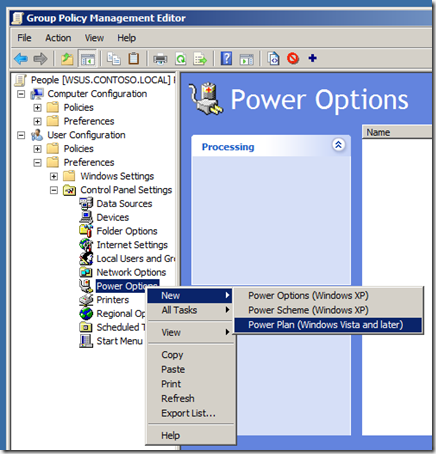
Step 2. Go to the Computer Configuration > Preferences > Control Panel Settings > Local User and Groups option (see Image 1.).
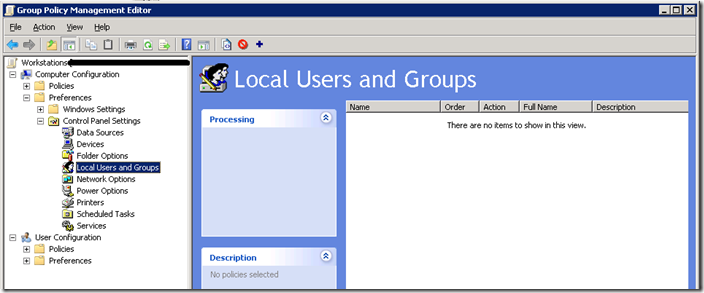 Image 1. Local User and Group
Image 1. Local User and Group
Step 3. Now click on Actions > New > Local Group
Step 4. Now you will be need to select “Administrators (built-in)” from the group name as this always selects the built-in administrators group even if you have renamed it to obfuscate the name of the admin account.
Step 5. Tick both “Delete all member users” and “Delete all member groups”. These two options will automatically remove any users or groups that are not explicitly being added to the group. You only need to do this on item number 1 in the list of settings as that setting will be processed last.
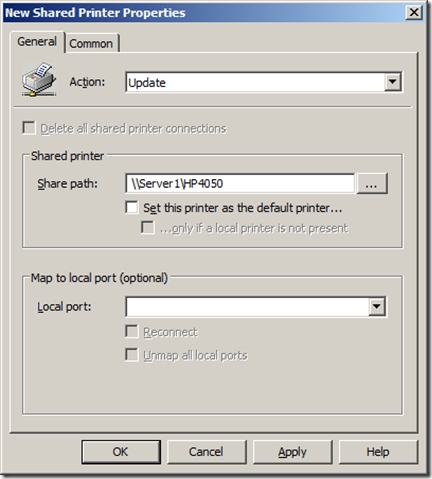
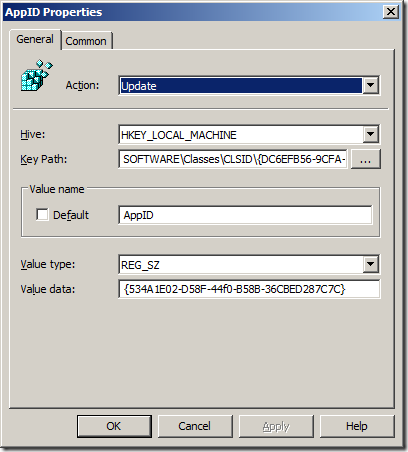
Step 6. Now you will need to make sure you have added back in the Domain Admin’s and Local Administrator groups so that you don’t totally lock yourself out of the computer. To do this click the “Add…” button to bring up the “Local Group Member” dialogue box (see Image 2)
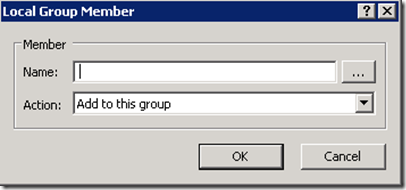 Image 2. Local Group Member
Image 2. Local Group Member
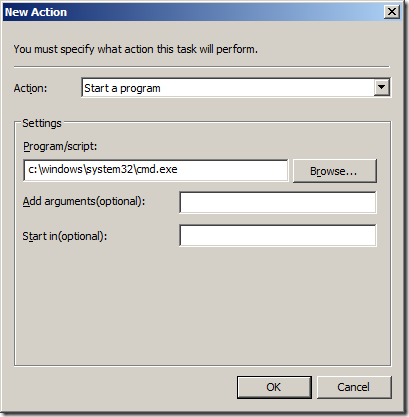
Step 7. Now type “BuiltIn\Administrators” in the Name field and click OK (see Image 3.)
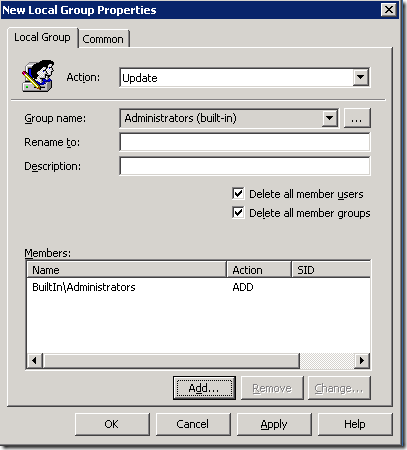 Image 3. Local Administrators group added to the local administrators group
Image 3. Local Administrators group added to the local administrators group
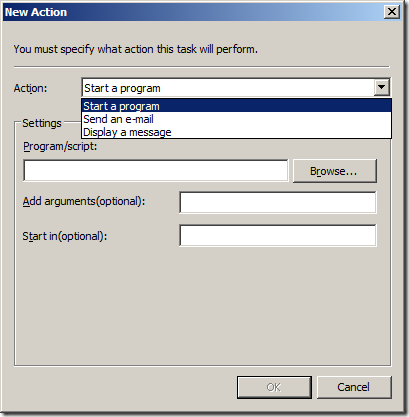
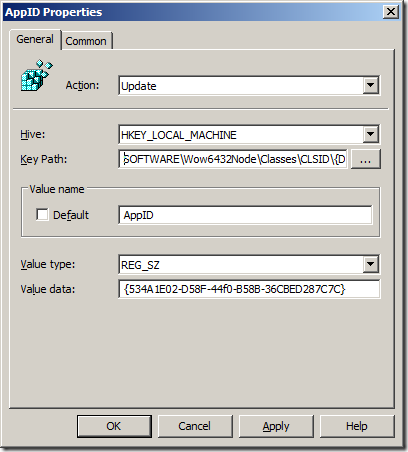
Step 8. You should also add “DOMAINNAME\Domain Admins” as it is a good practice to have the DA account as a member of the local admin group on all computers in the domain. To do this we are going to use the DomainName variables. Click “Add…” again and now click in the “Name:” text field and then press F3. This will now bring up the “Select Variable” dialogue box (See Image 4.). Click on the “DomainName” field and press “Select” and then “OK”. (alternatively you could type %DomainName% in the name field and just press OK.)
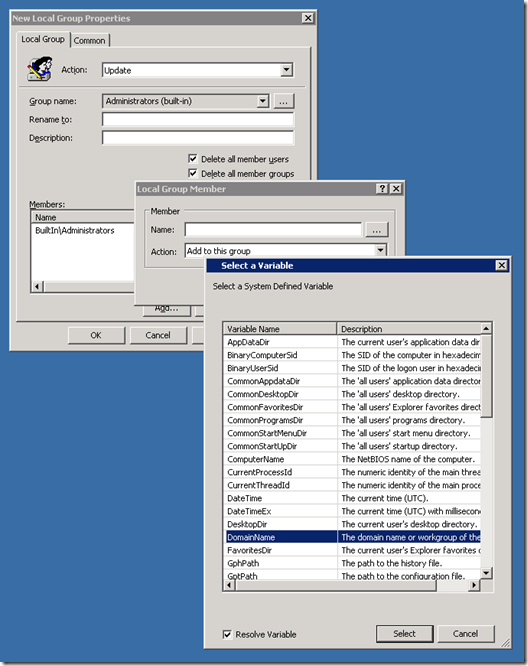 Image 4. Selecting the DomainName Variable
Image 4. Selecting the DomainName Variable
You should now see the following which will restrict the local administrator group to only have the Domain Admins and the local administrator.
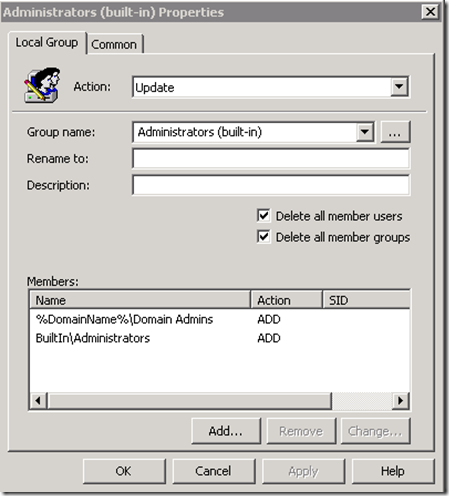 Image 5. Basic local administration group setting
Image 5. Basic local administration group setting
So what you as? I can do this already with the “Restricted Groups” Group Policy setting. Well only having the local Administrator and Domain Admin’s in the local admin group is not not much use unless you are willing to give everyone the local admin password or give them all Domain Admin’s privileges (Like that ever happens) when ever they needed admin access. Well again this is where Group Policy Preferences can help.
How to add individuals to a single computer?
Now we are going to go thorough how to add a uniquely named domain group to the local administrators group without having to set up multiple group policies objects. This scenario is very helpful if you want to grant a single user or group local administrators access on computer but still ensure that no other users or groups can be added without explicitly being approved. In the steps below the computer name is DESKTOP01 and the domain name is CONTOSO, we want to add the group “CONTOSO\DESKTOP01 Administrators” to the local administrator group but we also want the same to happen on DESKTOP02, DESKTOP03 and so on, each with their own uniquely named group based on the computer name.
Step 9. First go back and repeat steps 1 to 6 until you get to the Local Group Member dialogue box (see Image 6.)
 Image 6. Add Local Group Member
Image 6. Add Local Group Member
Step 10. Type “%DomainName%\%ComputerName% Administrators” in the Name text field and click “OK” (Image 7.)
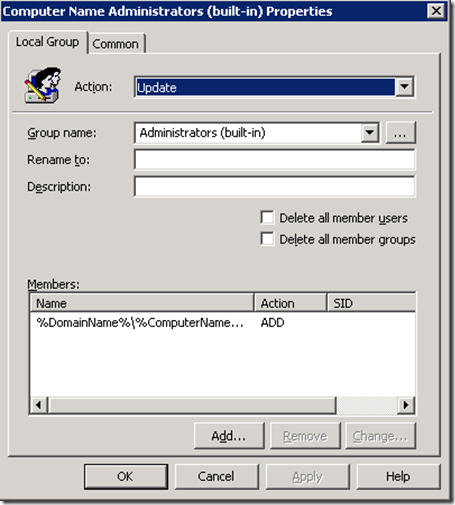 Image 7. Configuration to automatically unique group to local administrators group
Image 7. Configuration to automatically unique group to local administrators group
Now this will now automatically add a domain group called “
DOMAINNAME\
COMPUTERNAME Administrators” to the local administrators group on the computer to which the policy is applied.
This group policy setting combined with the other setting made earlier (see Image 5.) will mean that the local administrator group on the computer DESKTOP01 in the CONTOSO domain will have the following members automatically added to the group:
- CONTOSO\Domain Admins
- DESKTOP01\Administrators
- CONTOSO\DESKTOP01 Administrators
But ANY other users or groups will be automatically removed after the next group policy refresh. This does mean there is a slight window of opportunity for someone to slip in an un-authorised account into the local administrators group but they will get removed at the next policy update.
Side Note: I have found that users almost never complain that they cant add un-authorised user to the local admin account on computer. Go figure…

However the “CONTOSO\DESKTOP01 Administrators” group will only be added to the local administrators group on the computer DESKTOP01 if that group is already exists. Therefore you do not need to create the group until the need arises to add an individual user or group to just a single computer.
AWSOME!!!! I hear you say… but wait there is more…
How do I add additional broader groups to the local administrators group?
Now that you are able to granuarlly add a single user or group to the local administrators group on a computer you might run into problems id you have more than a 1000 computers due to
AD Token Bloat Issues . So to get around this we can setup some more broadly applied administrator groups to the computer that will give admin access to only a subset of computers such as all workstations or only the SQL Servers in your organisation.
Workstations Admin Groups
To apply a Workstation administrators group to the local administrators group on all workstations make sure you have a group policy only targeted to your workstations. This is normally pretty easy as most companies isolate their workstations computer accounts to one (or a select) number of Organisational Unit.
Step 11. Go back and repeat steps 6 and 7 but this time add the group “%DomainName%”\Workstations Administrators” in the name field. This will added the additional group “CONTOSO\Workstation Administrators” to the local admin group on all the workstations in your domain which will allow you to easily add all the Desktop Administrators in your organisation access to all the workstations without having to give them the local admin password or domain admin’s privileges.
Server Role Admin Groups
It gets a little tricker when you want to grant access to a server based on its role as server are sometime configured for multiple roles. So in these steps we are going to automatically added a domain group called “CONTOSO\SQL Server Administrators” to all the servers you have that have SQL Server installed on them. This will be very handy to making sure SQL service accounts or database administrators have admin access to all the servers that have Microsoft SQL Server installed. You can however make multiple version of these admin group for other roles (e.g. Exchange,SCCM,ISA) you just need to know what the best way to target the setting.
Step 12. First make sure you are editing a group policy that is applied to all your servers in your organisation.
Step 13. Repeat Step 9 and 10 and then we open the properties of the new policy setting and specify the group but this time we type “%DomainName%\SQL Server Administrators” in the name field.
Step 14. Click on the “Common” tab and then tick “Item Level Targeting” and click the “Targeting…” button.
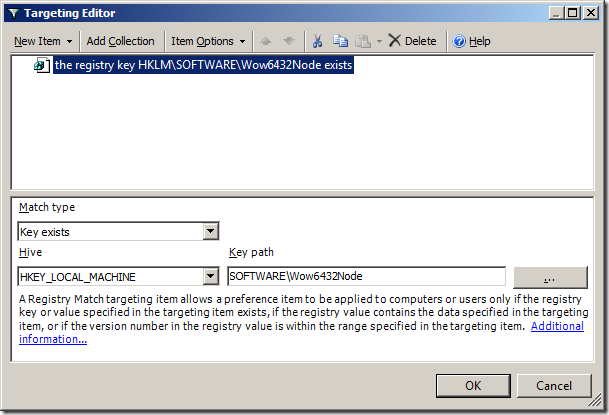
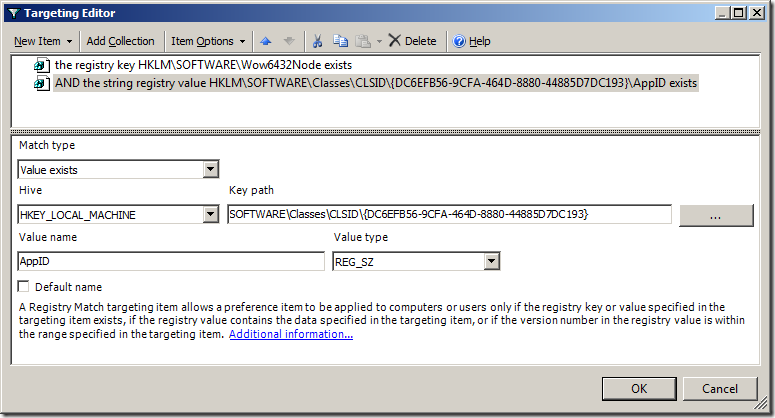
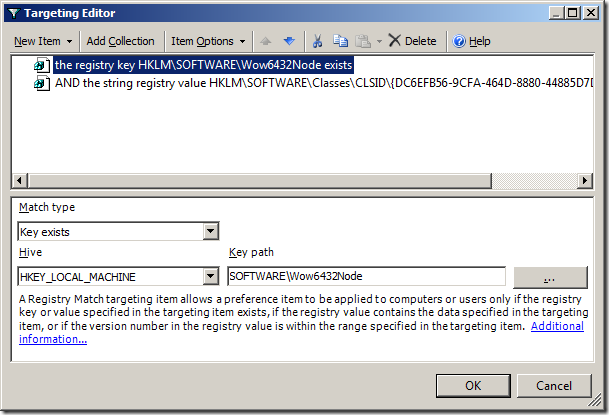
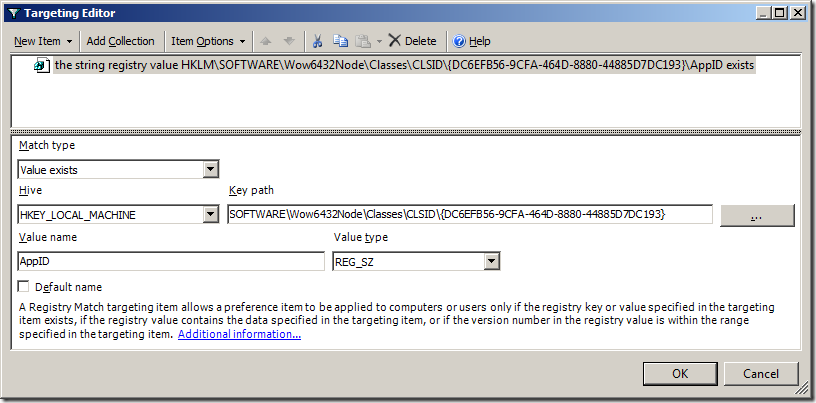
Step 15. Click on the “New Item” in the menu bar and select the option you want to use to target all the SQL servers in your organisation and select the “File Match” option to look in the Program Files folder and see if a sub-folder exists called “Microsoft SQL Servers” (See Image 8). This is normally true for any server that has Microsoft SQL Server installed and so it will then automatically apply the SQL Server Admin group to that server if it was installed.
Note: In this example we tested that the “Microsoft SQL Server” folder exists but we could also make rule to test for the existence of a particular file or registry key.
 Image 8. Testing to see if Microsoft SQL Server is installed.
Image 8. Testing to see if Microsoft SQL Server is installed.
Now any computer that SQL Server, MSDE or SQL Express installed will get the group “CONTOSO\SQL Server Administrators” automatically added to the local admin group.
This nice thing about this is that if SQL is installed on the server at some point in the future the SQL Admin group will be added automatically at the next group policy refresh without you having to do a thing.
Finally.. now you have tight control of the local administrator groups on all the computers in your domain it is now important to monitor and secure the domain groups that are being added to the local administrator groups as they now control who has admin access to all your computers. But I will save how to do that for another blog post…
Download as PDF


 LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks