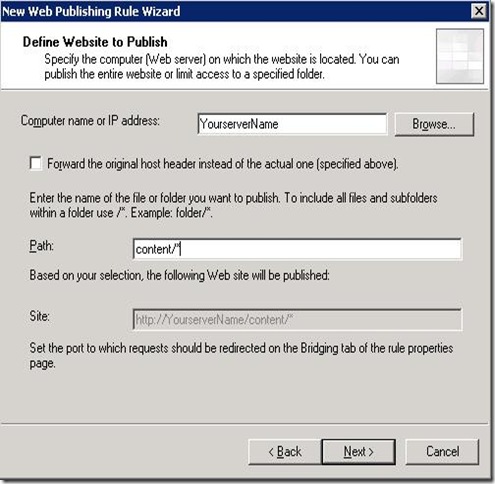
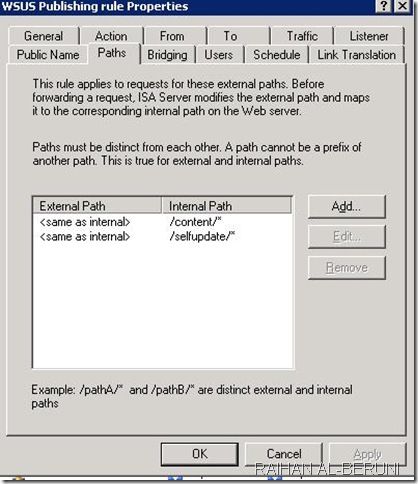
کد:
http://araihan.wordpress.com/2010/02/17/wsus-how-to-configuring-a-wsus-server-to-use-branchcache/
What is branchCache? BranchCache™ is a new feature in Windows® 7 and Windows Server® 2008 R2 that can reduce wide area network (WAN) or bandwidth utilization and enhance network application responsiveness when users access content in a central office from branch office locations. When you enable BranchCache, a copy of the content that is retrieved from the Web server or file server is cached within the branch office. If another client in the branch requests the same content, the client can download it directly from the local branch network without needing to retrieve the content by using the Wide Area Network (WAN).
How Branchcache works? When a Windows 7 Client from a branch office request data such as WSUS content to a head office Server then server check authentication and authorise data to pass on to the client. This is an ordinary communication happens without branchcache also.
But with branchcache, The client uses the hashes in the metadata to search for the file in the Hosted Cache server. Because this is the first time any client has retrieved the file, it is not already cached on the local network. Therefore, the client retrieves the file directly from the content server. The Hosted Cache server connects to the client and retrieves the set of blocks that it does not have cached.
When a second Windows 7 client from the same branch requests the same WSUS content from the content server or WSUS server. The content server authorizes the user/client and returns content identifiers. The second client uses these identifiers to request the data from the Hosted Cache server residing in branch. This time, it does not retrieve data from the DFS share residing in head office.
To configure a Web server or an application server that uses the Background Intelligent Transfer Service (BITS) protocol, you must install the BranchCache feature using server manager. To configure a file server to use BranchCache, you must install the BranchCache for Network Files feature and configure the server using Group Policy. This article discuss and show how to configure WSUS to use branchcache. The followings are the steps involve in head office and Branch Offices.
Head Office:
- Install and configure back end SQL Server
- Create DFS share
- Install and configure front end WSUS Server
- Configure GPO for WSUS client
Branch Office:
- Install and configure Branchcache File Server
- Configure GPO for Branchcache
- Install and configure front end WSUS server
- Configure GPO for WSUS client
Installing BranchCache File Server
1. Click Start, point to Administrative Tools, and then click Server Manager.
2. Right-click Roles and then click Add Roles.
3. In the Add Features Wizard, select File Server and BranchCache for network files and then click Next.
4. In the Confirm Installation Selections dialog box, click Install.
5. In the Installation Results dialog box, confirm that BranchCache installed successfully, and then click Close.
Using Group Policy to configure BranchCache
1. Open the Group Policy Management Console. Click Start, point to Administrative Tools, and then click Group Policy Management Console.
2. Select the domain in which you will apply the Group Policy object, or select Local Computer Policy.
3. Select New from the Action menu to create a new Group Policy object (GPO).
4. Choose a name for the new GPO and click OK.
5. Right-click the GPO just created and choose Edit.
6. Click Computer Configuration, point to Policies, Administrative Templates, Network, and then click Lanman Server.
7. Double-click Hash Publication for BranchCache.
8. Click Enabled.
9. Under Options, choose one of the following Hash publication actions:
a. Allow hash publication for all file shares.
b. Allow hash publication for file shares tagged with “BranchCache support.”
c. Disallow hash publication on all file shares.
10. Click OK.
Using the Registry Editor to configure disk use for stored identifiers
1. Open an elevated command prompt (click Start, click All Programs, click Accessories, right-click Command Prompt, and then click Run as administrator).
2. At the command prompt, type Regedit.exe, and then press Enter.
3. Navigate to HKLM\CurrentControlSet\Service\LanmanServer\Parame ters.
4. Right-click the HashStorageLimitPercent value, and then click Modify.
5. In the Value box, type the percentage of disk space that you would like BranchCache to use. Click OK.
6. Close the Registry Editor.
Setting the BranchCache support tag on a file share
1. Click Start, point to Administrative Tools, and then click Share and Storage Management.
2. Right-click a share and then click Properties.
3. Click Advanced.
4. On the Caching tab, select Only the files and programs that users specify are available offline.
5. Select Enable BranchCache, and then click OK.
6. Click OK, and then close the Share and Storage Management Console.
To replicate cryptographic data
1.
Open an elevated command prompt (click Start, click All Programs, click Accessories, right-click Command Prompt, and then click Run as administrator).
2. At the command prompt, type netsh branchcache set key passphrase=“MY_PASSPHRASE”, and then press Enter. Choose a phrase known only to you. Repeat this process using the same phrase on all computers that are participating in the cluster.
Client configuration using Group Policy
1. Click Start, point to Administrative Tools, and click Group Policy Management Console.
2. In the console tree, select the domain in which you will apply the GPO.
3. Create a new GPO by selecting New from the Action menu.
4. Choose a name for the new GPO, and then click OK.
5. Right click the GPO you created and choose Edit.
6. Click Computer Configuration, point to Policies, Administrative Templates: Policy definitions (ADMX files) retrieved from the local machine, Network, and then click BranchCache.
7. Double-click Turn on BranchCache.
8. Click Enabled, and then click OK.
9. To use Distributed Cache mode, double-click Turn on BranchCache – Distributed Caching mode, click Enabled, and then click OK. or
To use Hosted Cache mode, double-click Turn on BranchCache – Hosted cache mode, click Enabled, and then click OK.
10. To enable BranchCache for SMB traffic, double-click BranchCache for network files, click Enabled, select a latency value under Options, and then click OK.
Configuring a Branch WSUS server to use BranchCache
In addition to enabling BranchCache in your environment, the WSUS server must be configured to store update files locally (both the update metadata and the update files are downloaded and stored locally on the WSUS server). This ensures that the clients get the update files from the WSUS server rather than directly from Microsoft Update.
Install SQL Server 2005/2008 with Management Studio Express on the back-end computer
- Click Start, point at All Programs, point at SQL Server 2005, point at Configuration Tools, and select SQL Server Surface Area Configuration.
- Choose Surface Configuration for Services and Connections.
- In the left window, click the Remote Connections node.
- Select Local and remote connections and then select Using TCP/IP only.
- Click OK to save the settings.
To ensure administrative permissions on SQL Server
- Start SQL Server Management Studio (click Start, click Run, and then type sqlwb).
- Connect to the SQL Engine on the server where SQL Server 2005 was installed in Step 1.
- Select the Security node and then select Logins.
- The right pane will show a list of the accounts that have database access. Check that the person who is going to install WSUS 3.0 on the front-end computer has an account in this list.
- If the account does not exist, then right-click the Logins node, select New Login, and add the account.
- Set up this account for the roles needed to set up the WSUS 3.0 database. The roles are either dbcreator plus diskadmin, or sysadmin. Accounts belonging to the local Administrators group have the sysadmin role by default.
Install Branch WSUS Server
To install WSUS on the front-end computer At the command prompt, navigate to the folder containing the WSUS Setup program, and type:
WSUSSetup.exe /q FRONTEND_SETUP=1 SQLINSTANCE_NAME=server\instance CREATE_DATABASE=0
Here, Server\instance is the name of the remote SQL server that is holding the instance of WSUS database. If you do not want silent installation then don’t use /q switch and follow
WSUS installation link
Important! Microsoft recommend 1GB free space for Systems Partition and 30GB for WSUS contents. But this minimum recommended space will create havoc when WSUS log, database log and content grow over the years. So, I used 50GB as systems partition and 100GB as WSUS contents in DFS share.
To configure the proxy server on WSUS front-end servers
- In the WSUS administration console, select Options, then Update Source and Proxy Server.
- Select the Proxy Server tab, then enter the proxy server name, port, user name, domain, and password, then click OK.
- Repeat this procedure on all the front-end WSUS servers.
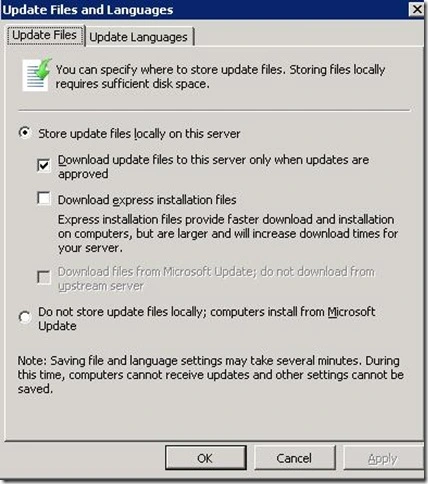
To specify where updates are stored
- In the left pane of the WSUS Administration console, click Options.
- In Update Files and Languages, click the Update Files tab.
- If you want to store updates in WSUS, select the Store update files locally on this server check box.
To specify whether updates are downloaded during synchronization or when the update is approved
- In the left pane of the WSUS Administration console, click Options.
- In Update Files and Languages, click the Update Files tab.
- If you want to download only metadata about the updates during synchronization, select the Download updates to this server only when updates are approved check box.
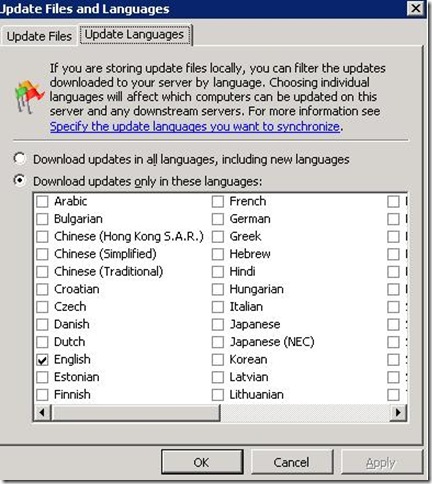
To specify language options
- In the left pane of the WSUS Administration console, click Options.
- In Update Files and Languages, click the Update Languages tab.
- In the Advanced Synchronization Options dialog box, under Languages, select one of the following language options, and then click OK.
- Select Download updates only in these languages: This means that only updates targeted to the languages you select will be downloaded during synchronization.
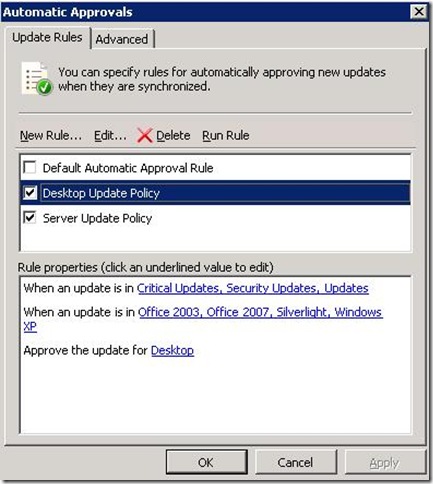
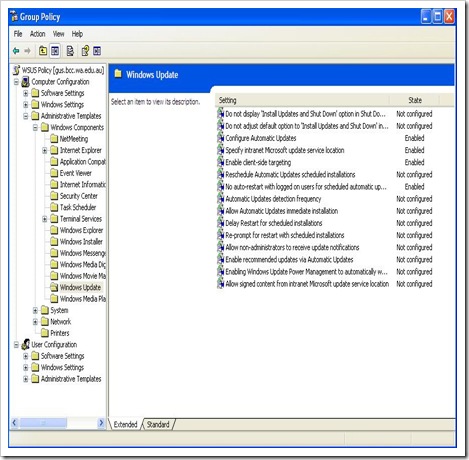
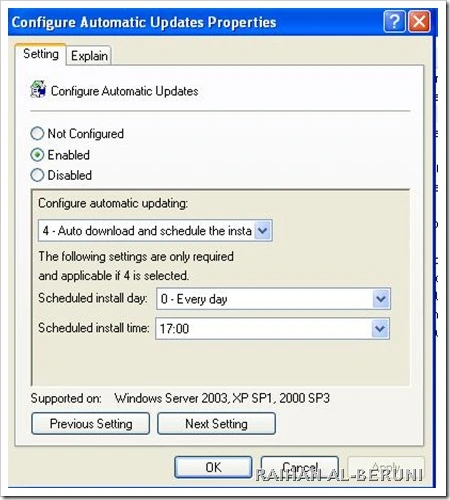
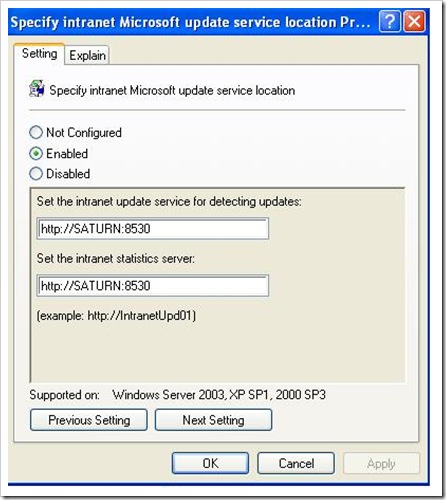
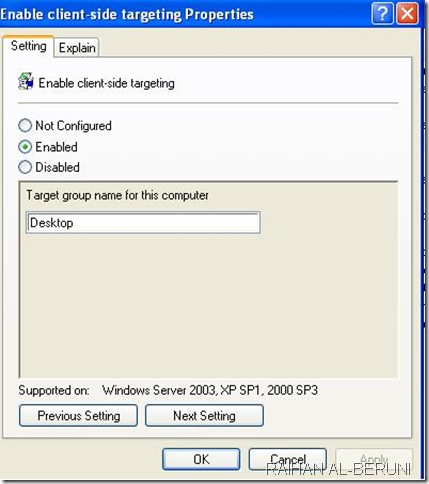
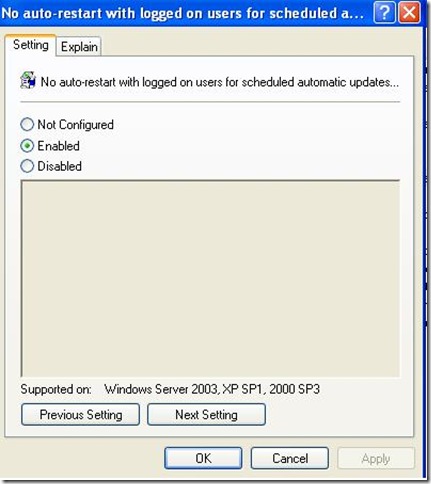
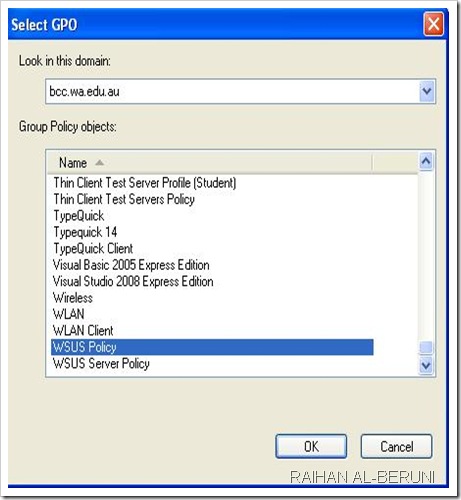
How to configure automatic updates by using Group Policy
Log on to Domain Controller using Administrative Privilege. Open GPO management Console>Select Organisational unit>Right client>create and link a new GPO> Name it as WSUS policy>right click>Edit. Go to Computer Configuration\Administrative Templates\Windows Components\Windows Updates\
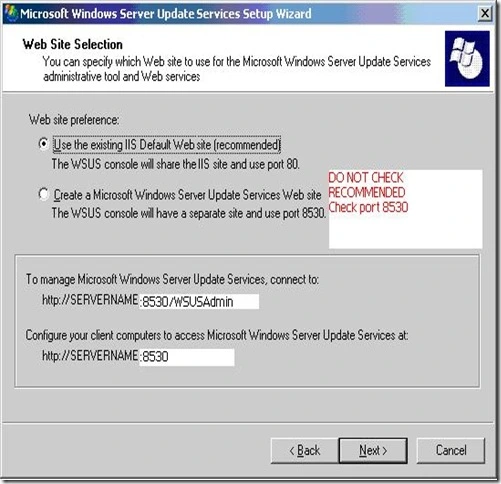
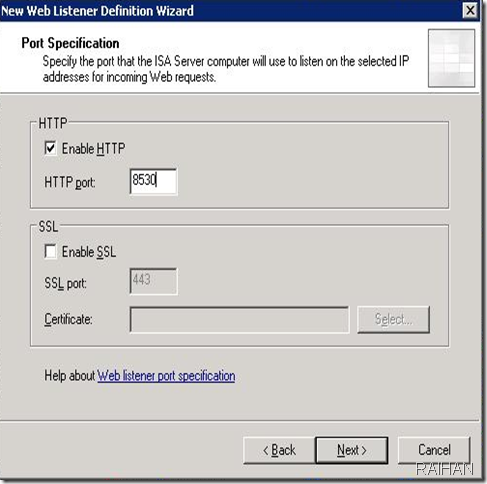
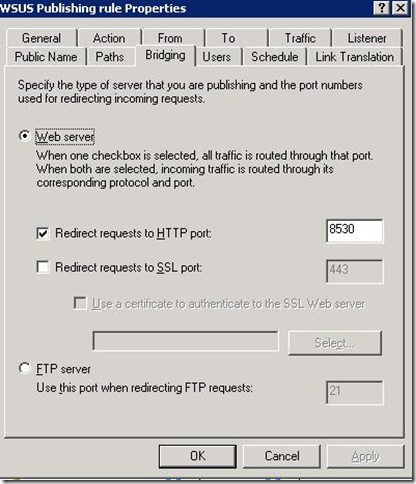
Now Specify Client target group, Intranet update server location i.e. http://servername:8530 , update schedule, installation schedule.
To set up a DFS share
Note:This DFS share will be used by all front end WSUS servers.
- Go to Start, point at All Programs, point at Administrative Tools, and click Distributed File System.
- You will see the Distributed File System management console. Right-click the Distributed File System node in the left pane and click New Root in the shortcut menu.
- You will see the New Root Wizard. Click Next.
- In the Root Type screen, select Stand-alone root as the type of root, and click Next.
- In the Host Server screen, type the name of the host server for the DFS root or search for it with Browse, and then click Next.
- In the Root Name screen, type the name of the DFS root, and then click Next.
- In the Root Share screen, select the folder that will serve as the share, or create a new one. Click Next.
- In the last screen of the wizard, review your selections before clicking Finish.
- You will see an error message if the Distributed File System service has not yet been started on the server. You can start it at this time.
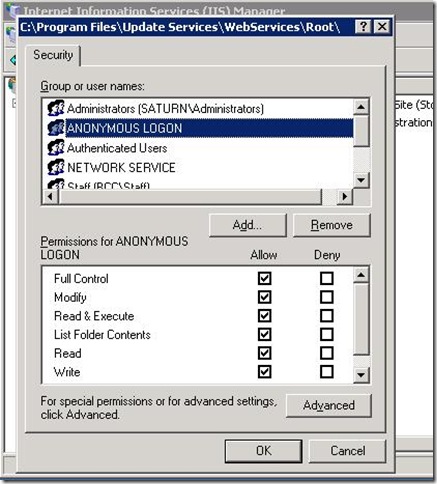
- Make sure that the domain account of each of the front-end WSUS servers has change permissions on the root folder of this share.
Important! If you are using a DFS share, be careful when uninstalling WSUS from one but not all of the front-end servers. If you allow the WSUS content directory to be deleted, this will affect all the WSUS front-end servers.
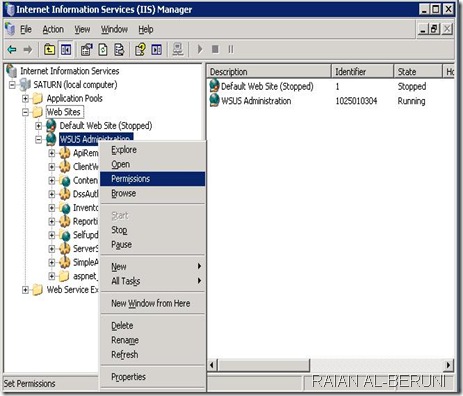
To configure IIS for remote access on the front-end WSUS servers
- On each of the servers, go to Start, point at All Programs, point at Administrative Tools, and click Internet Information Services (IIS) Manager.
- You will see the Internet Information Services (IIS) Manager management console.
- Click the server node, then the Web Sites node, then the node for the WSUS Web site (either Default Web Site or WSUS Administration).
- Right-click the Content node and select Properties.
- In the Content Properties dialog box, click the Virtual Directory tab. In the top frame you will see The content for this resource should come from:
- Select A share located on another computer and fill in the UNC name of the share.
- Click Connect As, and enter the user name and password that can be used to access that share.
- Be sure to follow these steps for each of the front-end WSUS servers that are not on the same machine as the DFS share.
To move the content directories on the front-end WSUS servers
- Open a command window.
- Go to the WSUS tools directory on the WSUS server:
cd \Program Files\Update Services\Tools - Type the following command:
wsusutil movecontent DFSsharename logfilename
where DFSsharename is the name of the DFS share to which the content should be moved, and logfilename is the name of the log file.
To configure Network Load Balancing
1. Enable Network load balancing
- a) Click Start, then Control Panel, Network Connections, Local Area Connection, and click Properties.
- b) Under This connection uses the following items, you may see an entry for Network Load Balancing. If you do not, click Install, then (on the Select Network Component Type screen) select Service, then click Add, then (on the Select Network Service screen) select Network Load Balancing, then OK.
- c) On the Local Area Connection Properties screen, select Network Load Balancing, and then click OK.
2. On the
Local Area Connection Properties screen, select
Network Load Balancing, and then click
Properties.
3. On the
Cluster Parameters tab, fill in the relevant information (the virtual IP address to be shared among the front end computers, and the subnet mask). Under
Cluster operation mode, select
Unicast.
4. On the
Host Parameters tab, make sure that the unique host identifier is different for each member of the cluster.
5. On the
Port Rules tab, make sure that there is a port rule specifying single affinity (the default). (Affinity is the term used to define how client requests are to be directed. Single affinity means that requests from the same client will always be directed to the same cluster host.)
6. Click
OK, and return to the
Local Area Connection Properties screen.
7. Select
Internet Protocol (TCP/IP) and click
Properties, and then click
Advanced.
8. On the
IP Settings tab, under
IP addresses, add the virtual IP of the cluster (so that there will be two IP addresses). This should be done on each cluster member.
9. On the
DNS tab, clear the
Register this connection’s addresses in DNS checkbox. Make sure that there is no DNS entry for the IP address


 20سپاس
20سپاس
 LinkBack URL
LinkBack URL About LinkBacks
About LinkBacks